We’re happy to announce the release of Cerbero Suite 5.2 and Cerbero Engine 2.2!
In this post we summarize the most important new features.
Multi-Processing
The main feature of this release is the introduction of our multi-processing technology.
Our products make use of parallel processing in terms of multi-threading whenever possible, but there are limitations to the capabilities of multi-threading.
Some of the advantages offered by multi-processing are:
- Possible process isolation
- Increased stability for 3rd party components
- Overcoming the Global Interpreter Lock (GIL) in Python
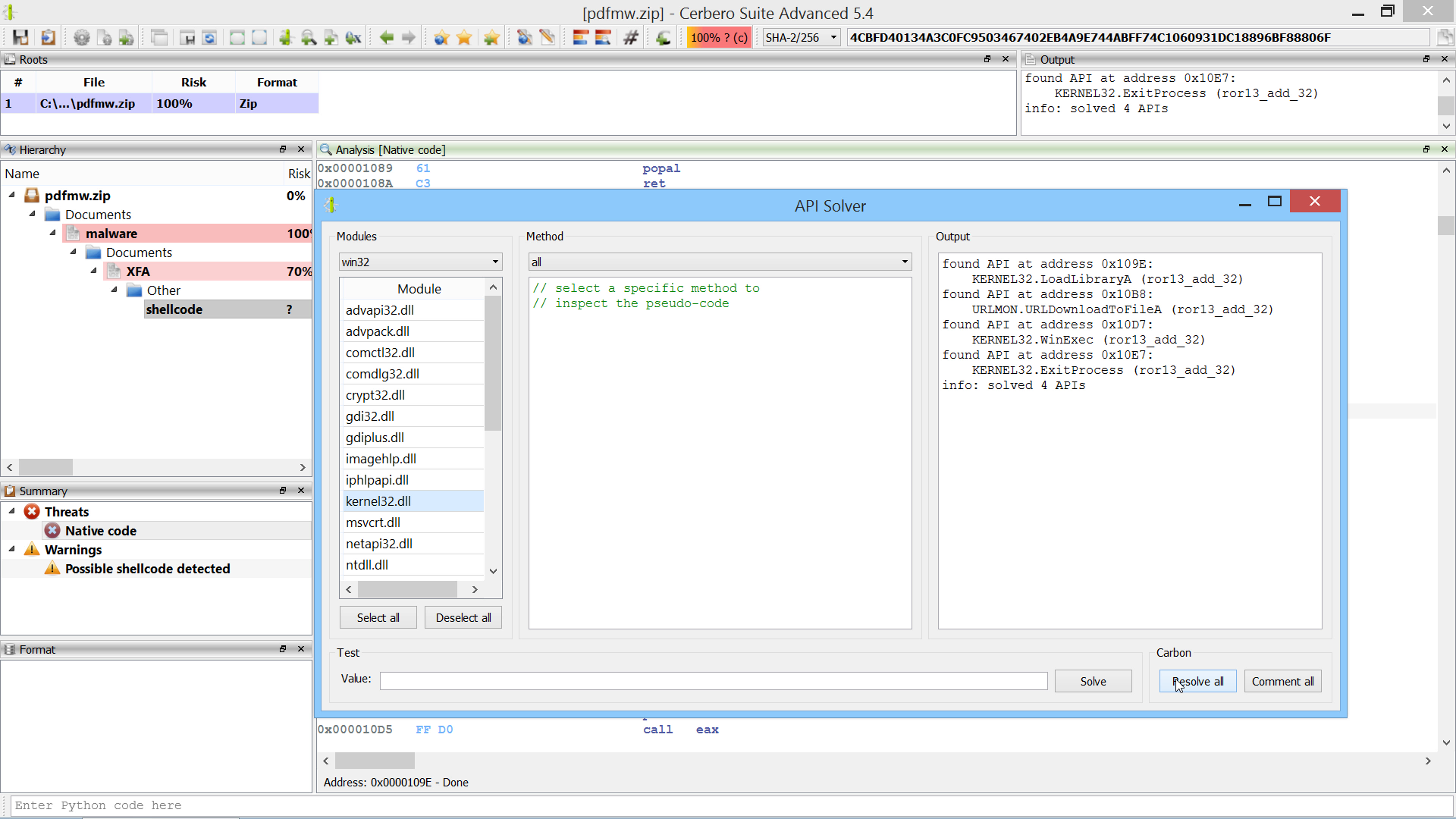
We have already detailed our multi-processing technology in two previous posts (part 1, part 2), but with this release we also fully documented the API.

Sleigh Decompiler Parallelization
We used our new multi-processing technology to parallelize the Sleigh decompiler by running it in a different process. This guarantees complete stability in case Sleigh encounters an issue and makes every decompiling operation safe to cancel.
We didn’t notice slow-downs by running the decompiler in a different process, in fact it’s still blazingly fast.
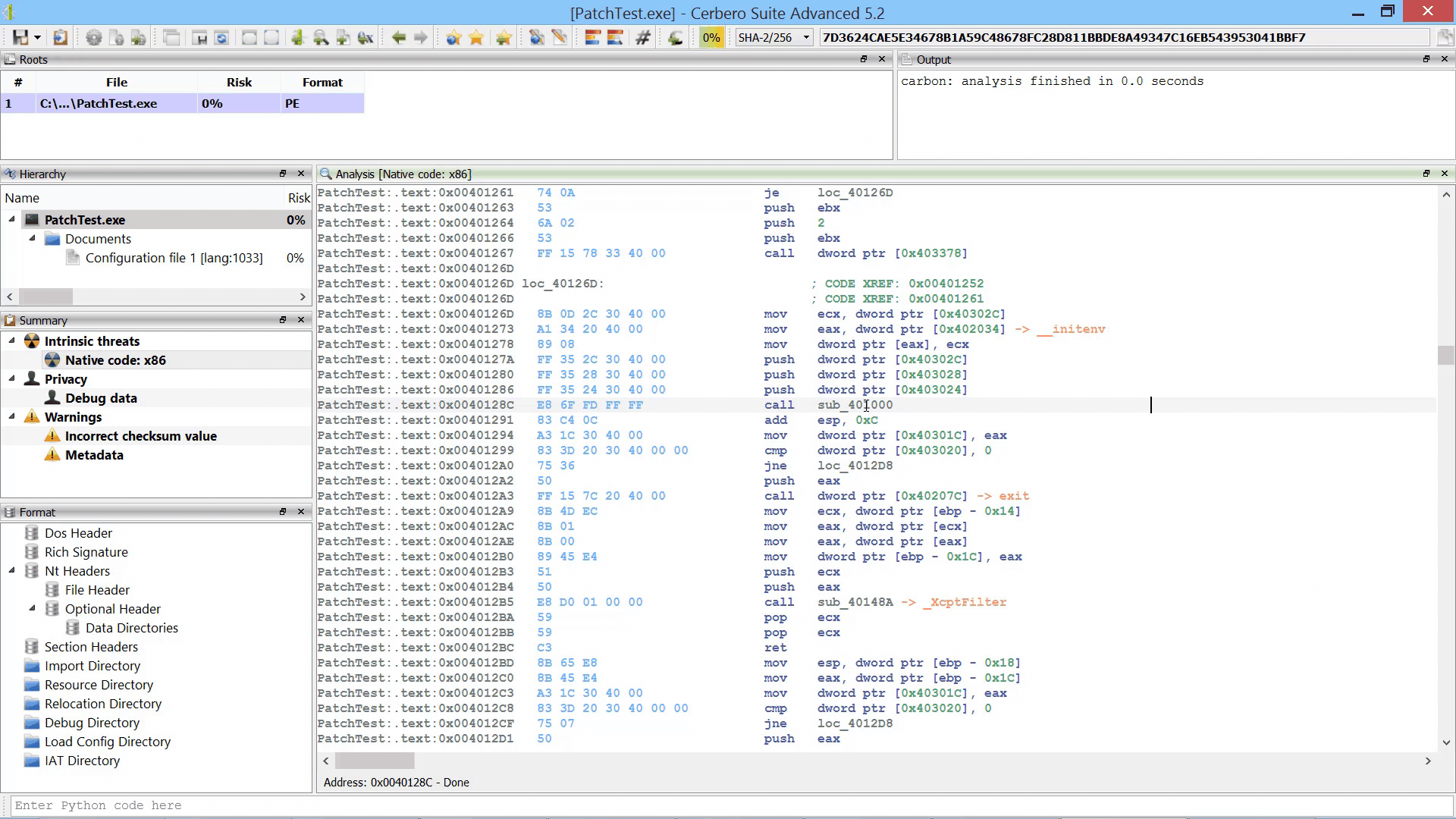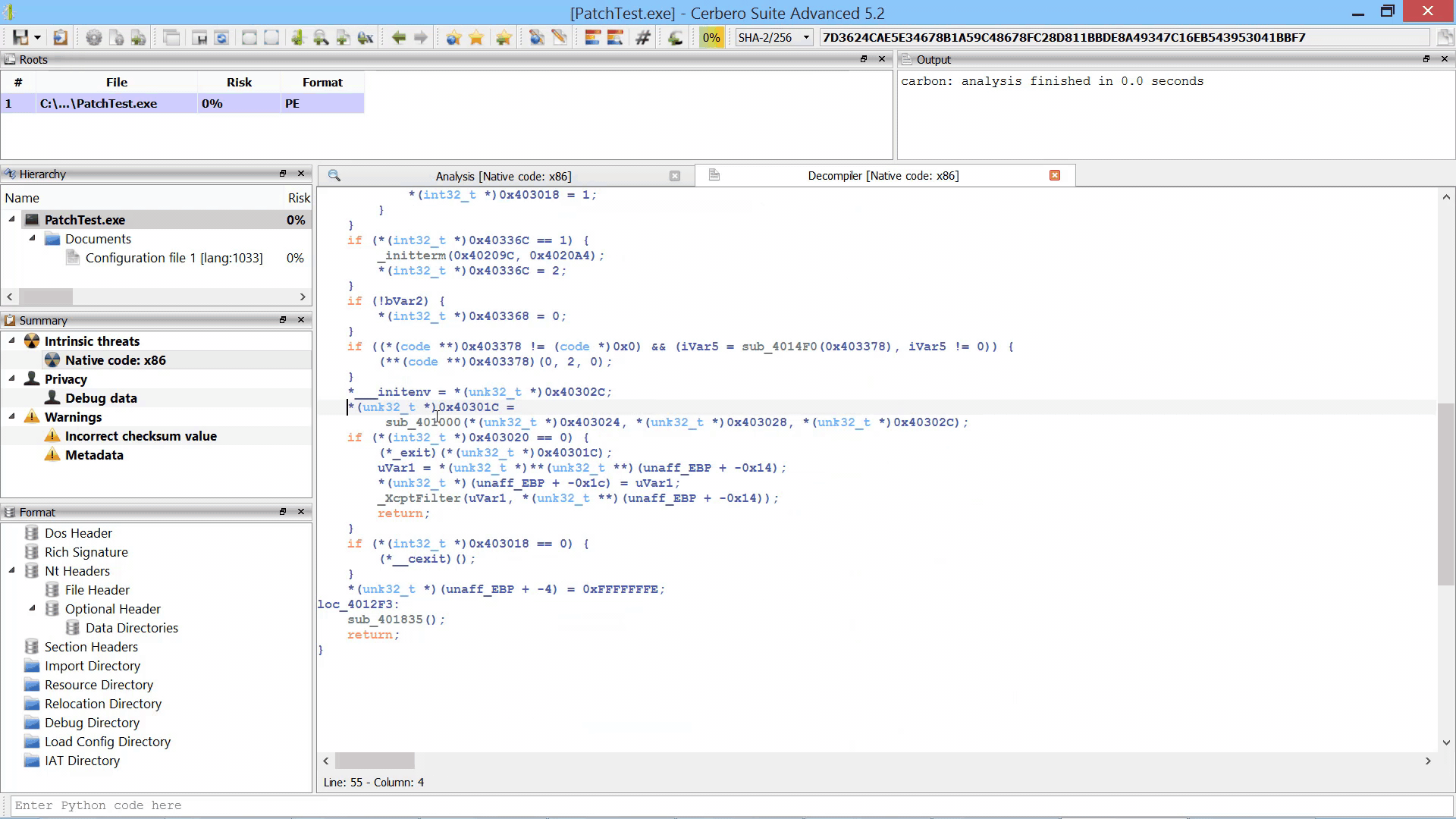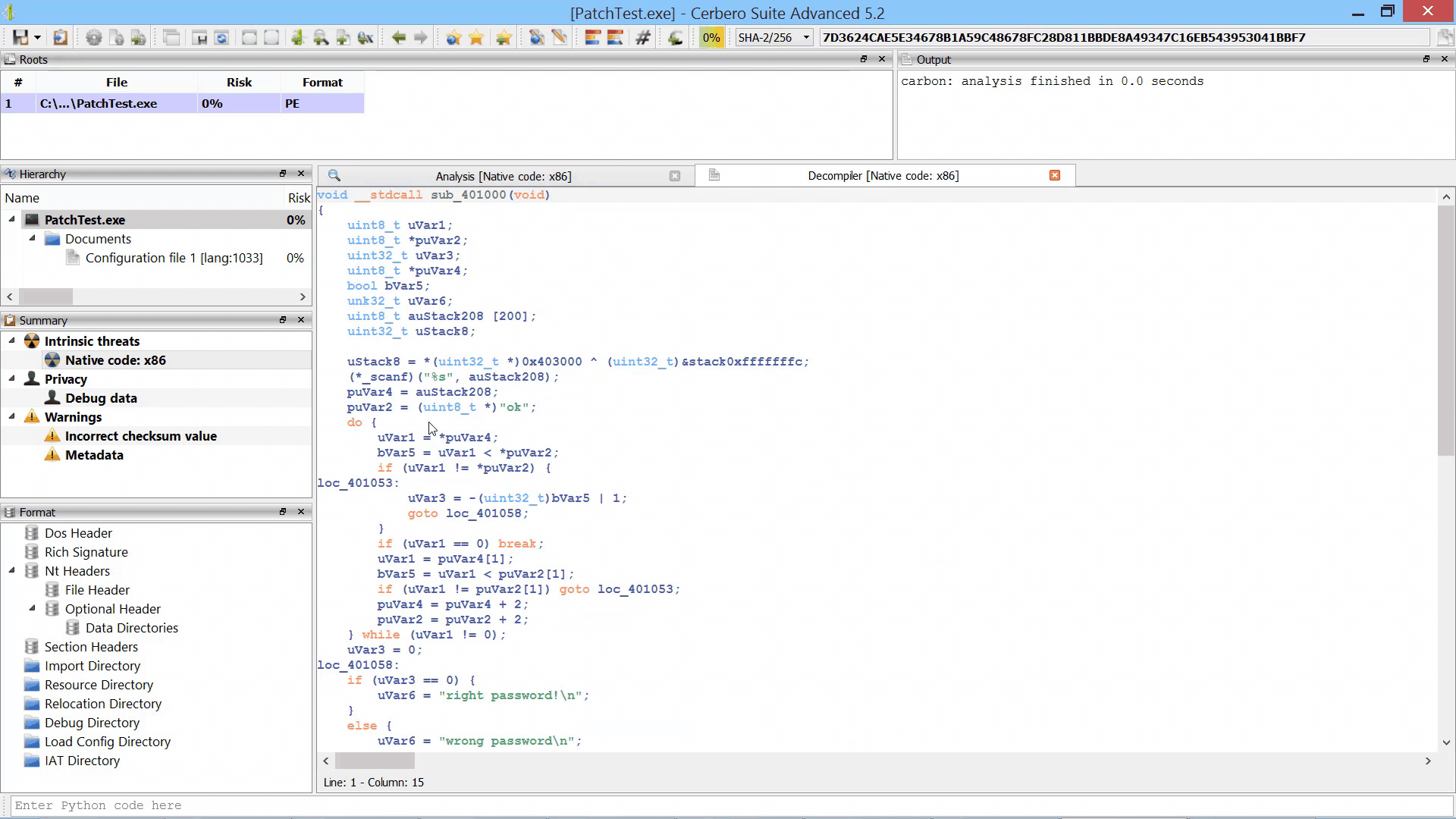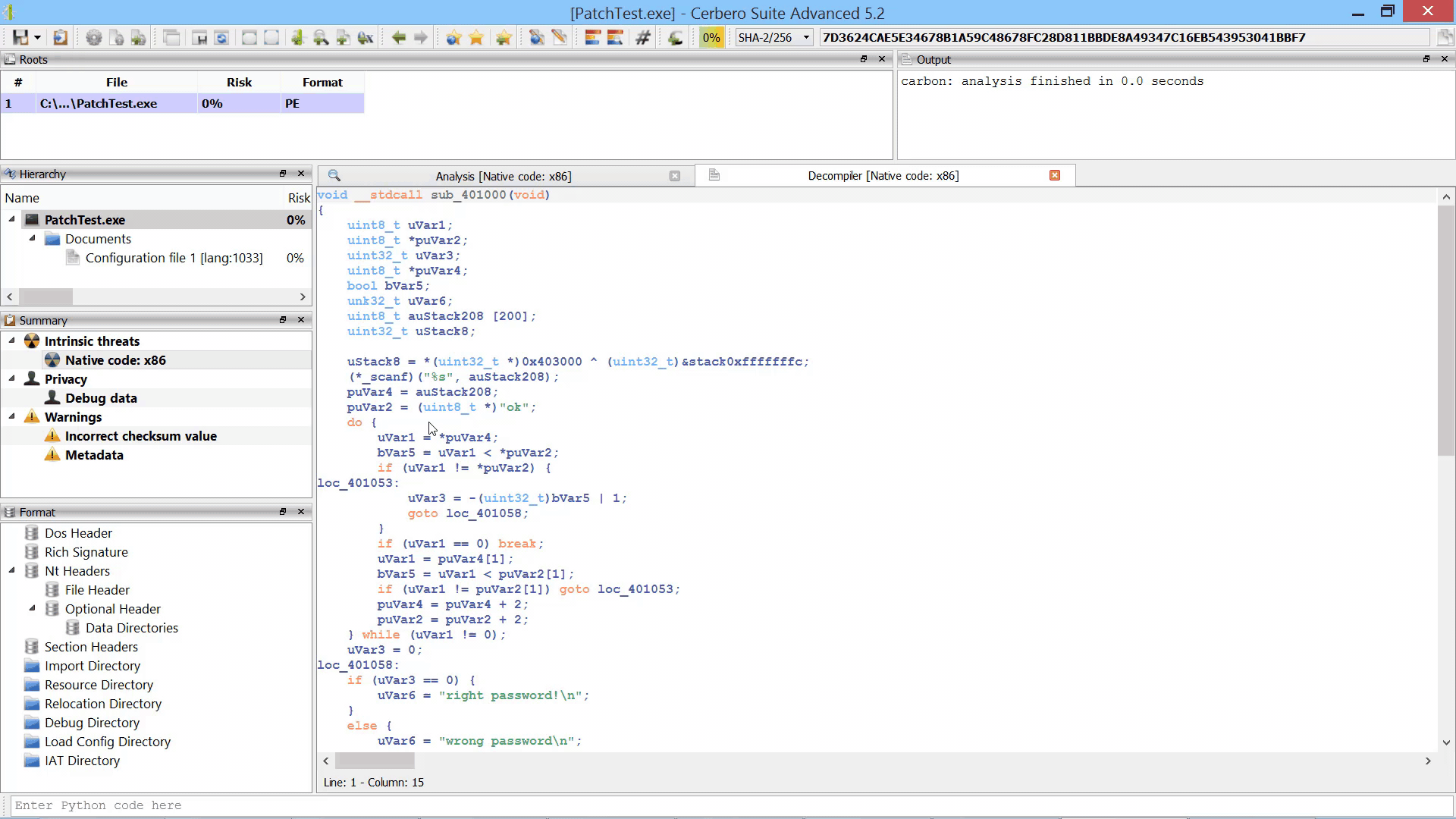
By parallelizing the decompiler we were also able to initialize it during the loading of the file/database. Thus, when the decompiler is invoked for the first time there is no initial delay.
Although the decompiler doesn’t take much time to load, the preloading makes it extra-snappy.
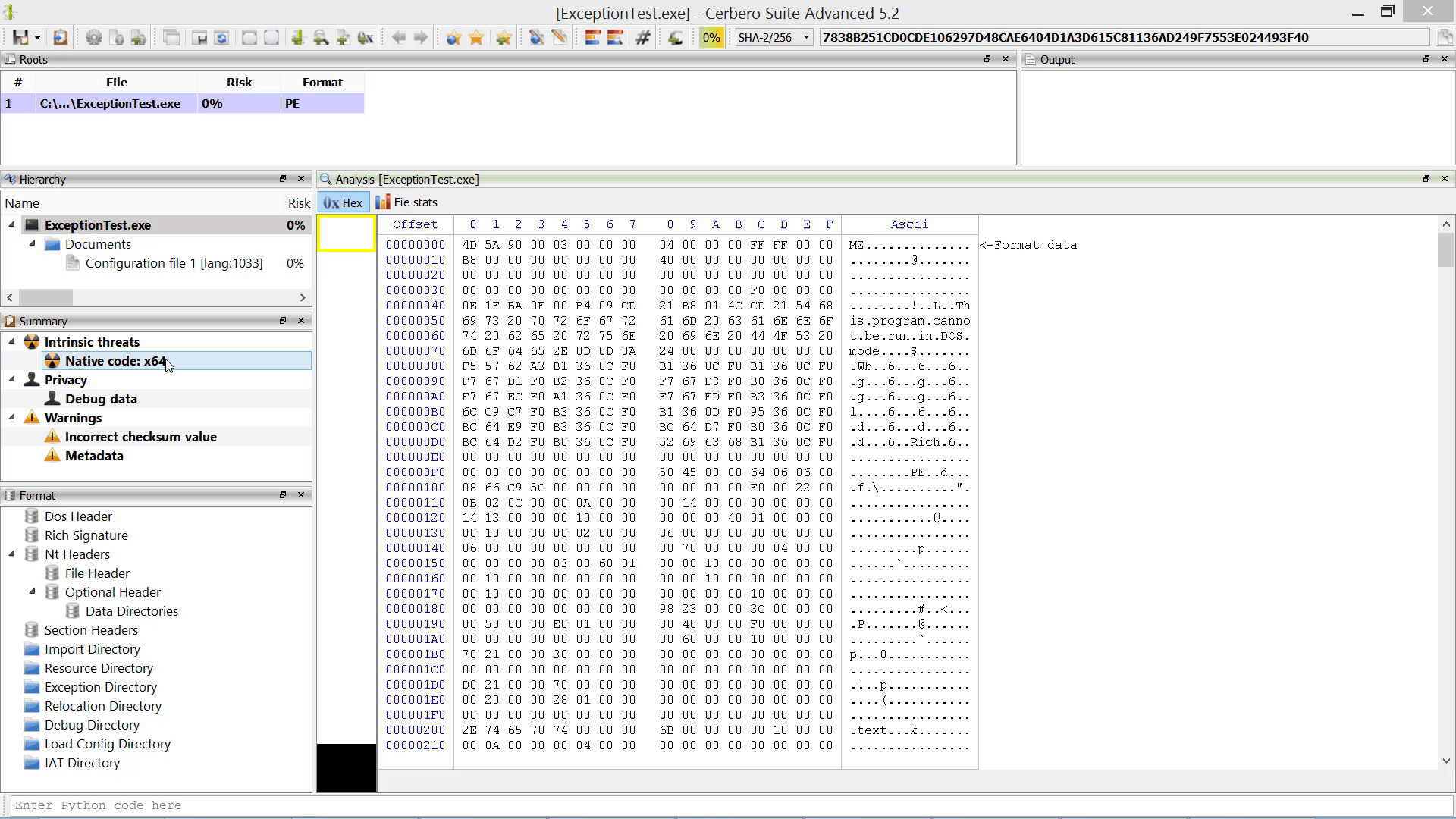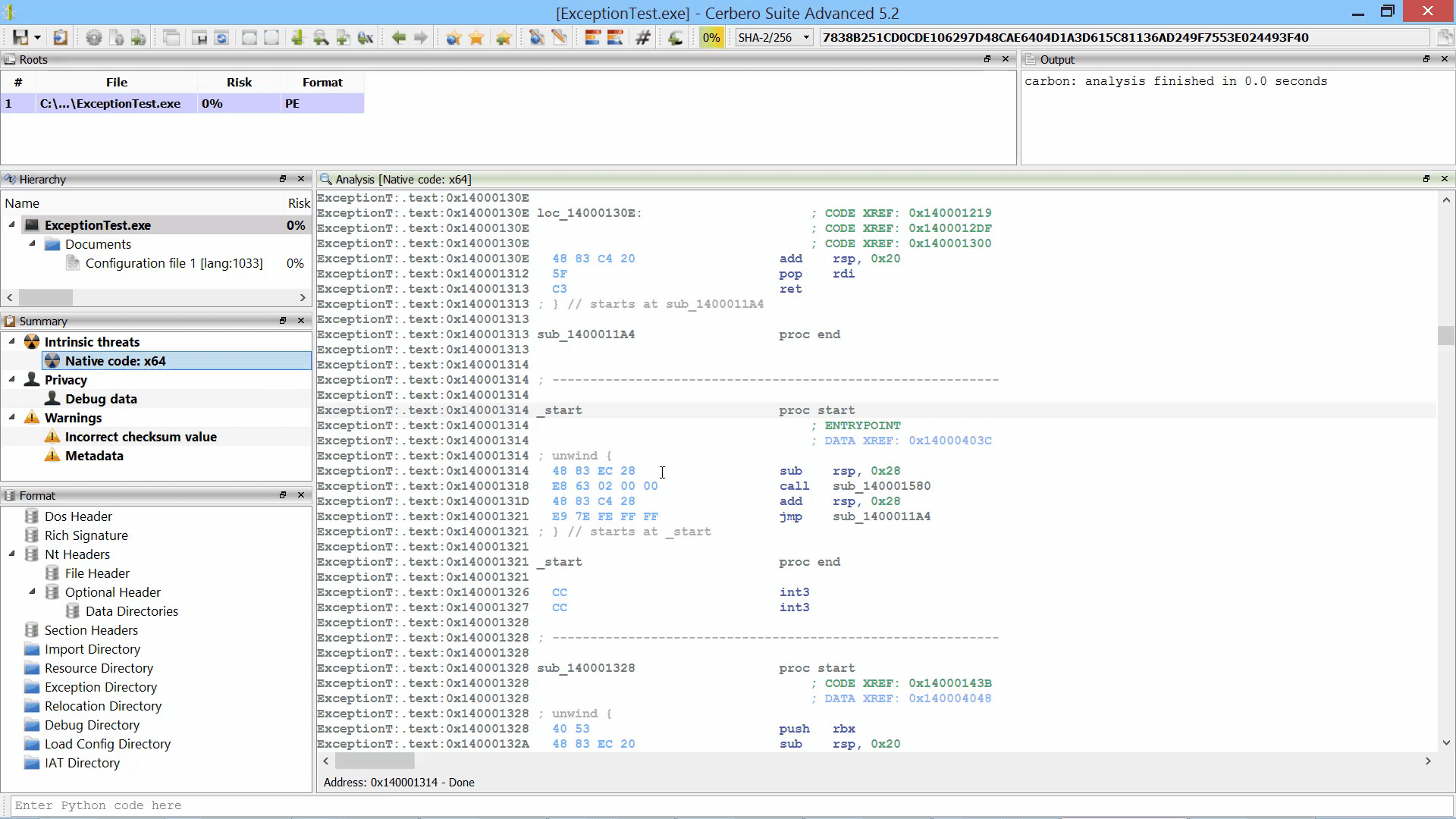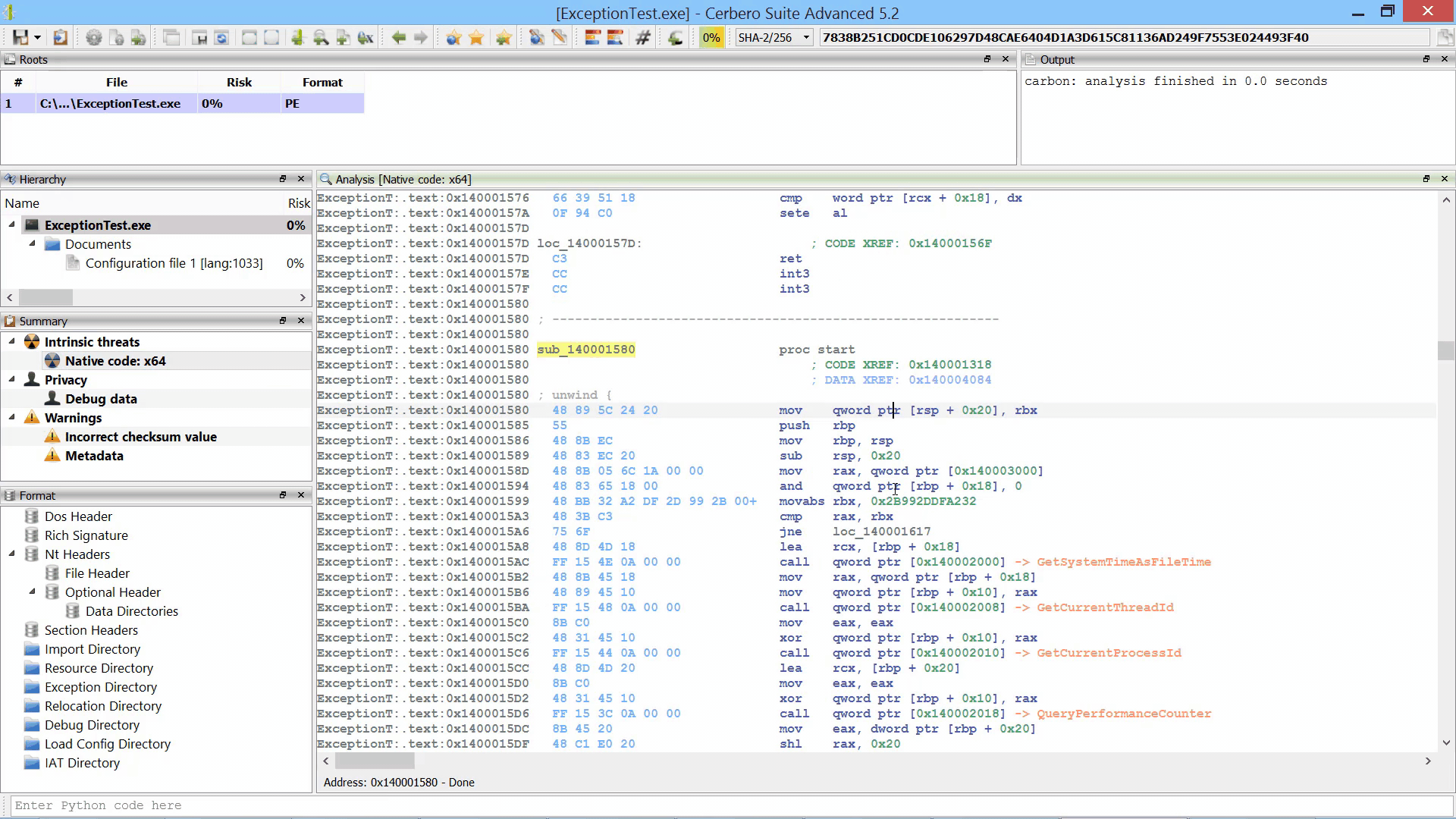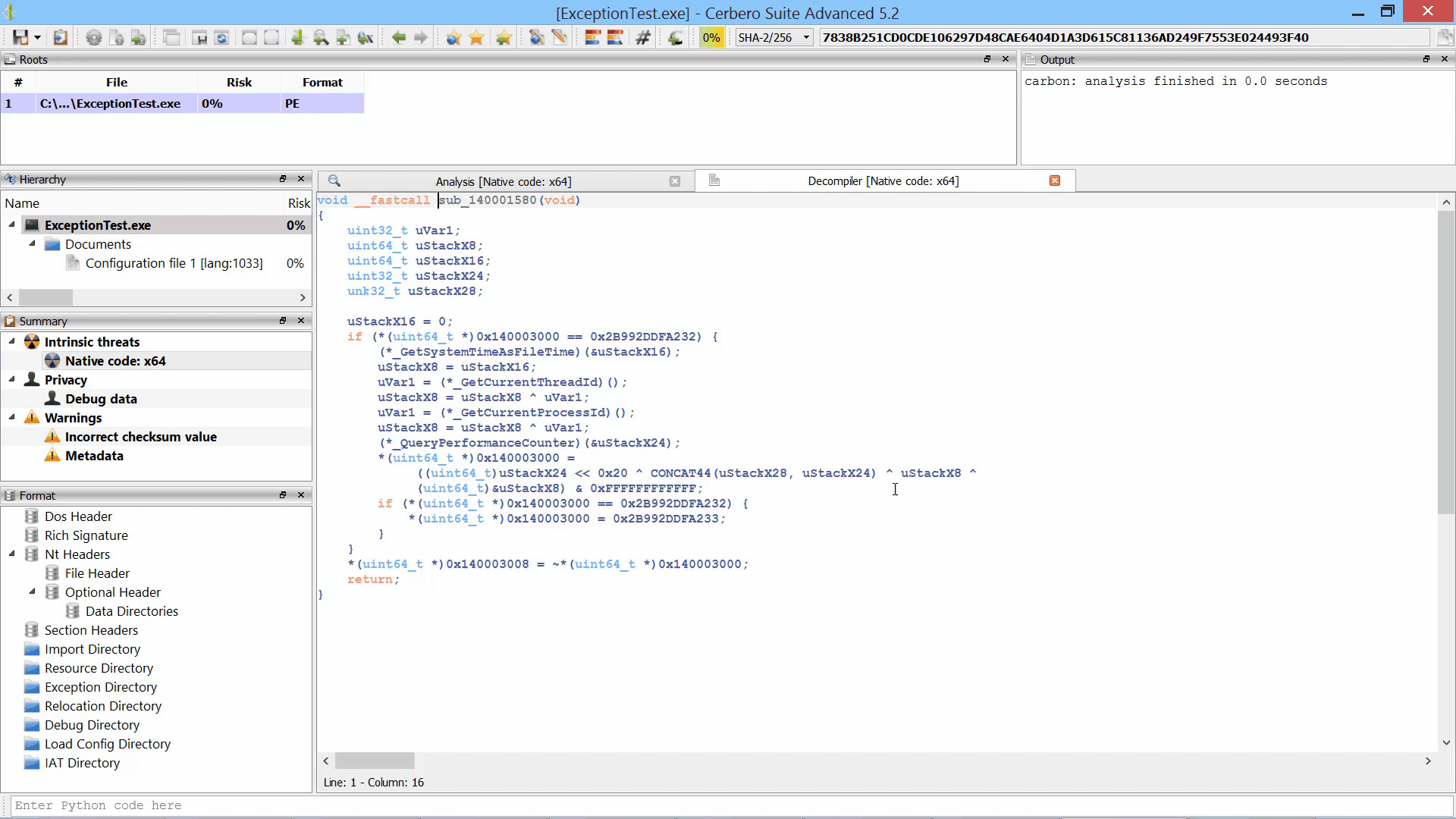
It is also possible to choose to run the decompiler in the same process as before from the Carbon settings.
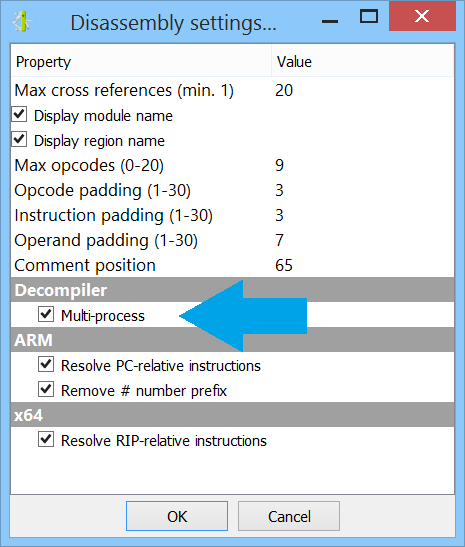
Carbon Documentation
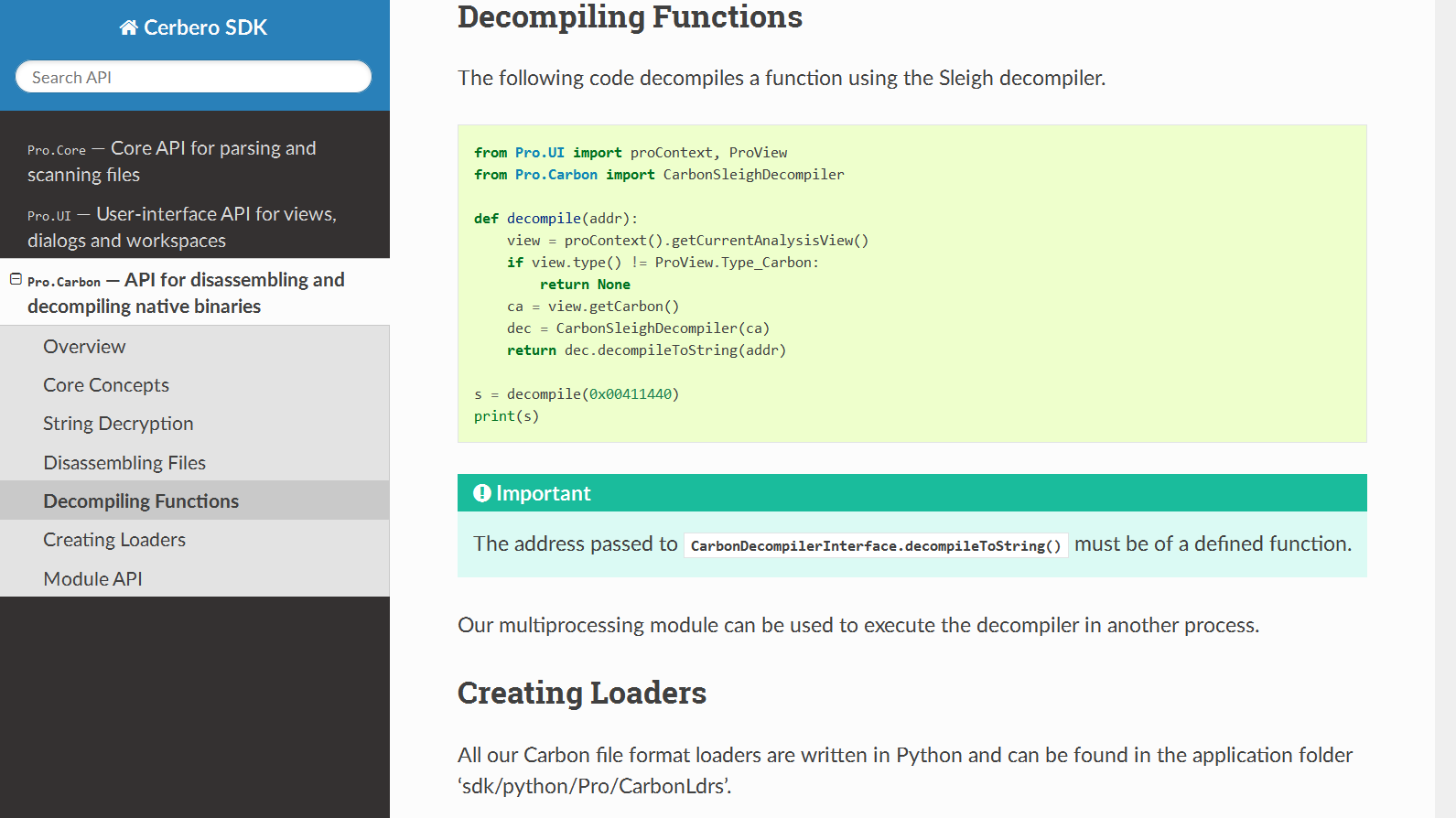
We have fully documented the Carbon API to disassemble and decompile native binaries.
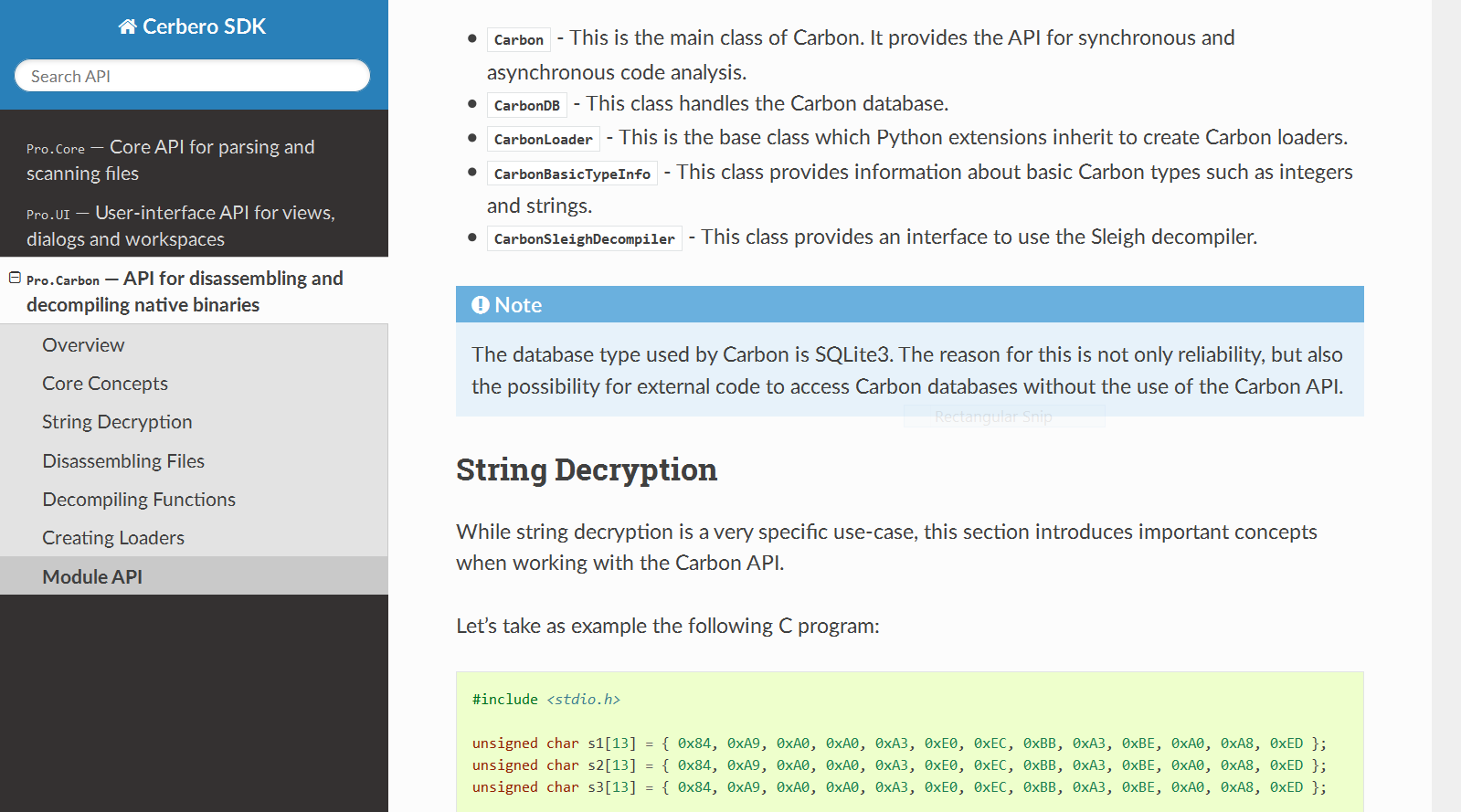
The documentation contains numerous code examples which cover the decryption of strings, disassembling of files, decompiling of functions and the creation of custom file loaders.
ZeroMQ Module
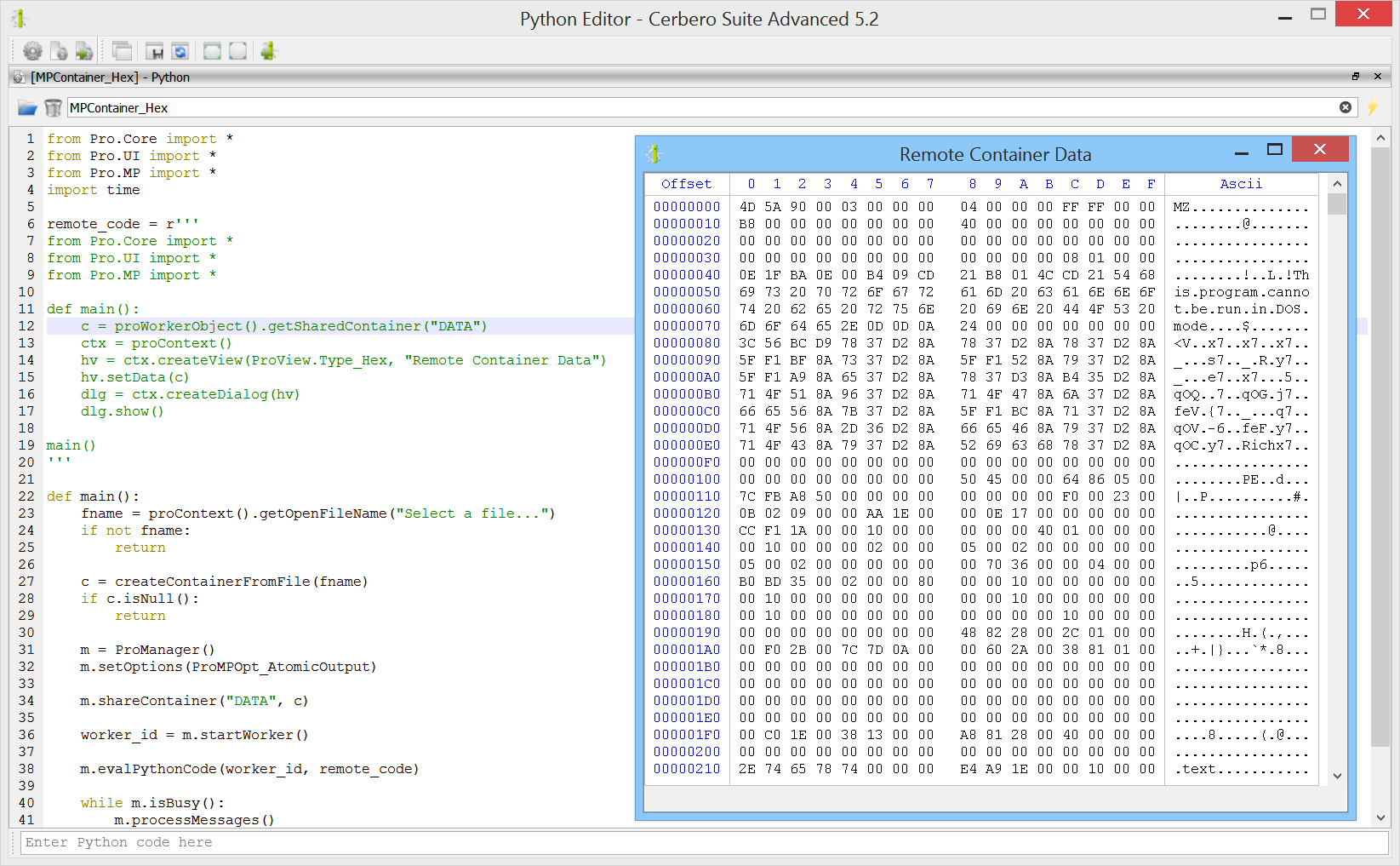
Our multi-processing technology relies on ZeroMQ. Therefore, we exposed ZeroMQ to our Python SDK.
Rather than using the provided Python wrappers, we exposed the C interface directly. We just added a few methods to convert from and to bytes objects in Python.
This is a basic client-server example using send/recv.
The client:
from Pro.zmq import *
import ctypes
context = zmq_ctx_new()
socket = zmq_socket(context, ZMQ_REQ)
zmq_connect(socket, "tcp://localhost:5555")
for i in range(1000):
zmq_send_bytes(socket, b"Hello, world!", 0)
print("info: sent")
zmq_close(socket)
zmq_ctx_destroy(context)
The server:
from Pro.zmq import *
context = zmq_ctx_new()
socket = zmq_socket(context, ZMQ_REP)
rc = zmq_bind(socket, "tcp://127.0.0.1:5555")
if rc == 0:
while True:
b = zmq_recv_bytes(socket, 13, 0)
print(b)
break
else:
print("error: couldn't bind to port")
zmq_close(socket)
zmq_ctx_destroy(context)
And this is a basic client-server example using messages.
The client:
from Pro.zmq import *
import ctypes
context = zmq_ctx_new()
socket = zmq_socket(context, ZMQ_REQ)
zmq_connect(socket, "tcp://localhost:5555")
msg = zmq_msg_t()
zmq_msg_init_bytes(msg, b"Hello, world!")
rc = zmq_msg_send(msg, socket, 0)
print(rc)
print("info: sent")
zmq_close(socket)
zmq_ctx_destroy(context)
The server:
from Pro.zmq import *
context = zmq_ctx_new()
socket = zmq_socket(context, ZMQ_REP)
rc = zmq_bind(socket, "tcp://127.0.0.1:5555")
if rc == 0:
msg = zmq_msg_t()
zmq_msg_init(msg)
while True:
# wait until a message is received
rc = zmq_msg_recv(msg, socket, 0)
if rc != -1:
print(zmq_msg_bytes(msg))
zmq_msg_close (msg)
break
else:
print("error: couldn't bind to port")
zmq_close(socket)
zmq_ctx_destroy(context)
Improved Logic Providers
We optimized logic provider extensions. In particular, it is now possible to specify the type option for standalone tools:
type = tool
When this option is specified, the init function of the logic provider must return False. This causes the logic provider to be treated as a standalone tool rather than a scan logic provider and avoids creating a scan report for it.
Improved Custom Views
We added the progress bar control and idle notifications to custom views. You can find both features documented on the SDK page of the UI module.
Finally, a thank you to Insid3Code Team for reporting three of the bugs we fixed in this release.