The last release of the Profiler featured some significant improvements. So while it also included initial PySide support, there wasn’t much time to make it really nice. One of the missing things was the ability to mix internal Profiler views (such as the hex editor) with PySide widgets. With the upcoming 0.9.2 release it will be possible to create a view and obtain a PySide widget with just one method:
widget = view.toWidget()
This way one can make use of advanced internal views of the Profiler and combine them with other custom controls. Let’s see a practical example.
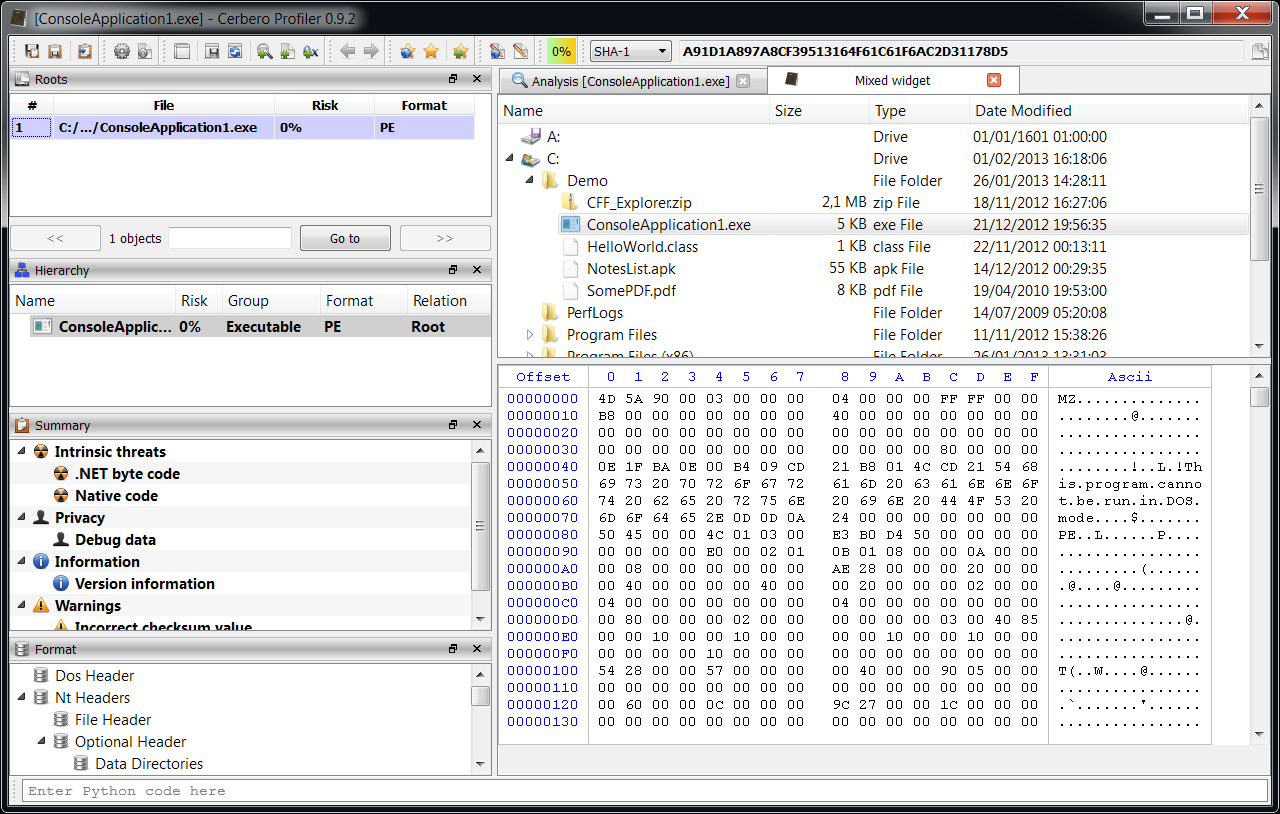
The widget in the screenshot combines a QTreeView with a directory model and a hex view. When a file is activated in the tree, it is opened by the hex editor. To try it out, just press Ctrl+Alt+R and enter the following code:
from Pro import *
from PySide import QtCore, QtGui
class MixedWidget(QtGui.QSplitter):
def __init__(self, parent=None):
super(MixedWidget, self).__init__(parent)
self.setWindowTitle("Mixed widget")
self.setOrientation(QtCore.Qt.Vertical)
self.model = QtGui.QDirModel()
tree = QtGui.QTreeView()
tree.setModel(self.model)
self.addWidget(tree)
ctx = proContext()
self.hex = ctx.createView(ProView.Type_Hex, "")
self.addWidget(self.hex.toWidget())
tree.activated.connect(self.updateFile)
def updateFile(self, idx):
if self.model.isDir(idx) == True:
self.hex.clear()
else:
name = self.model.filePath(idx)
self.hex.setFileName(name)
ctx = proContext()
w = MixedWidget()
v = ctx.createViewFromWidget(w)
ctx.addView(v)
Amazingly little code snippet, right? Please note that the ProHexView setFileName method is also a new addition to the SDK.