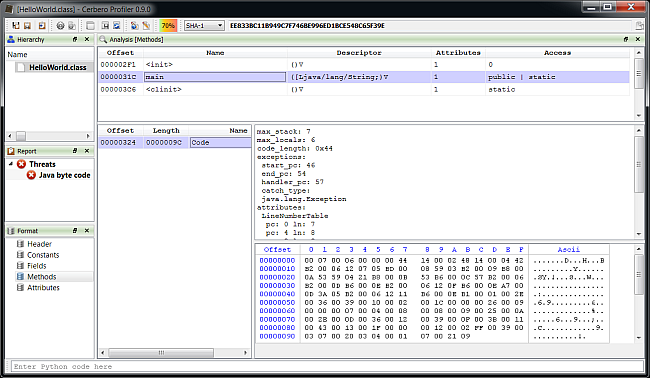
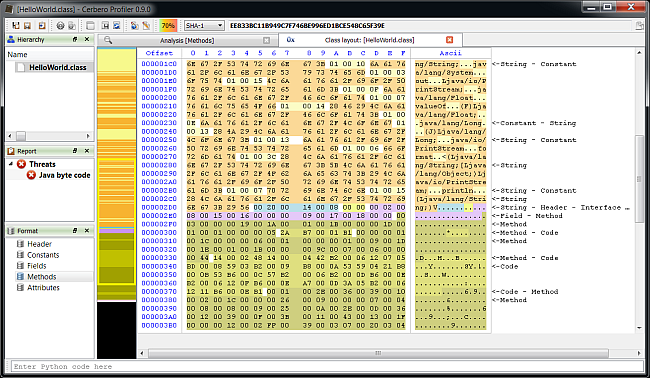
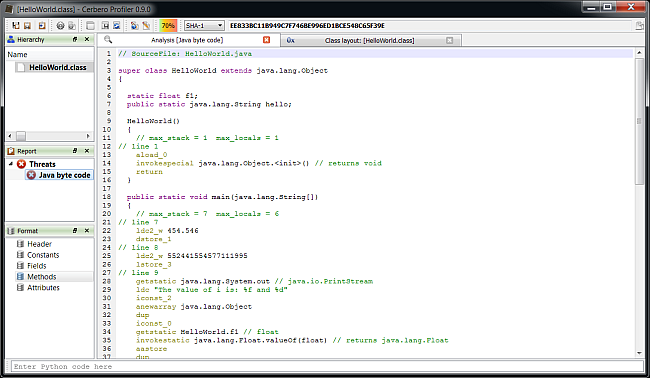
Support for Android’s DEX format is the last major feature of the upcoming 0.9.0 release of the Profiler. The support includes format, layout ranges and a Dalvik disassembler. Support for APK is implicit, since support for Zip archives has been added long ago.
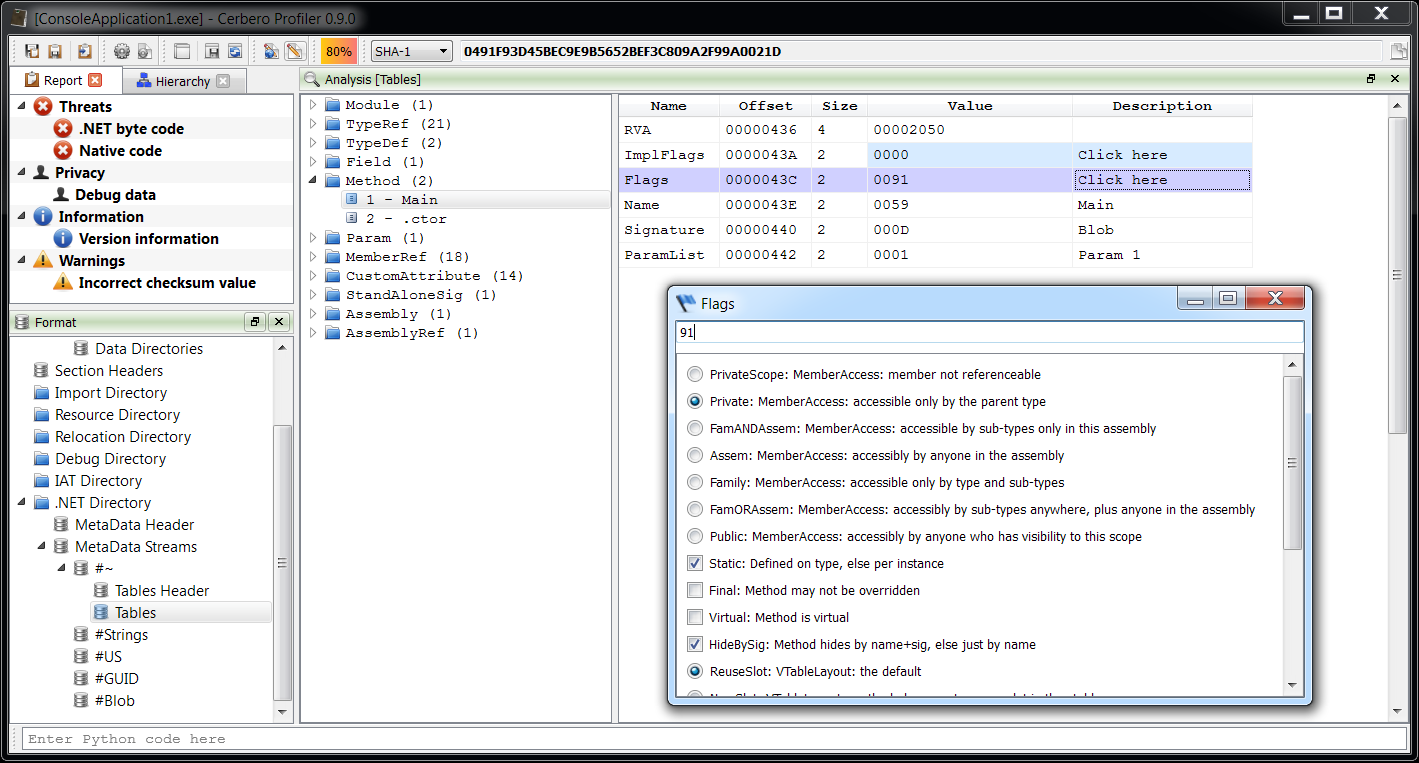
All sections of the format are accessible. The central point for parsing a DEX file is the Classes view. Hence it’s also the most complex view of the format.
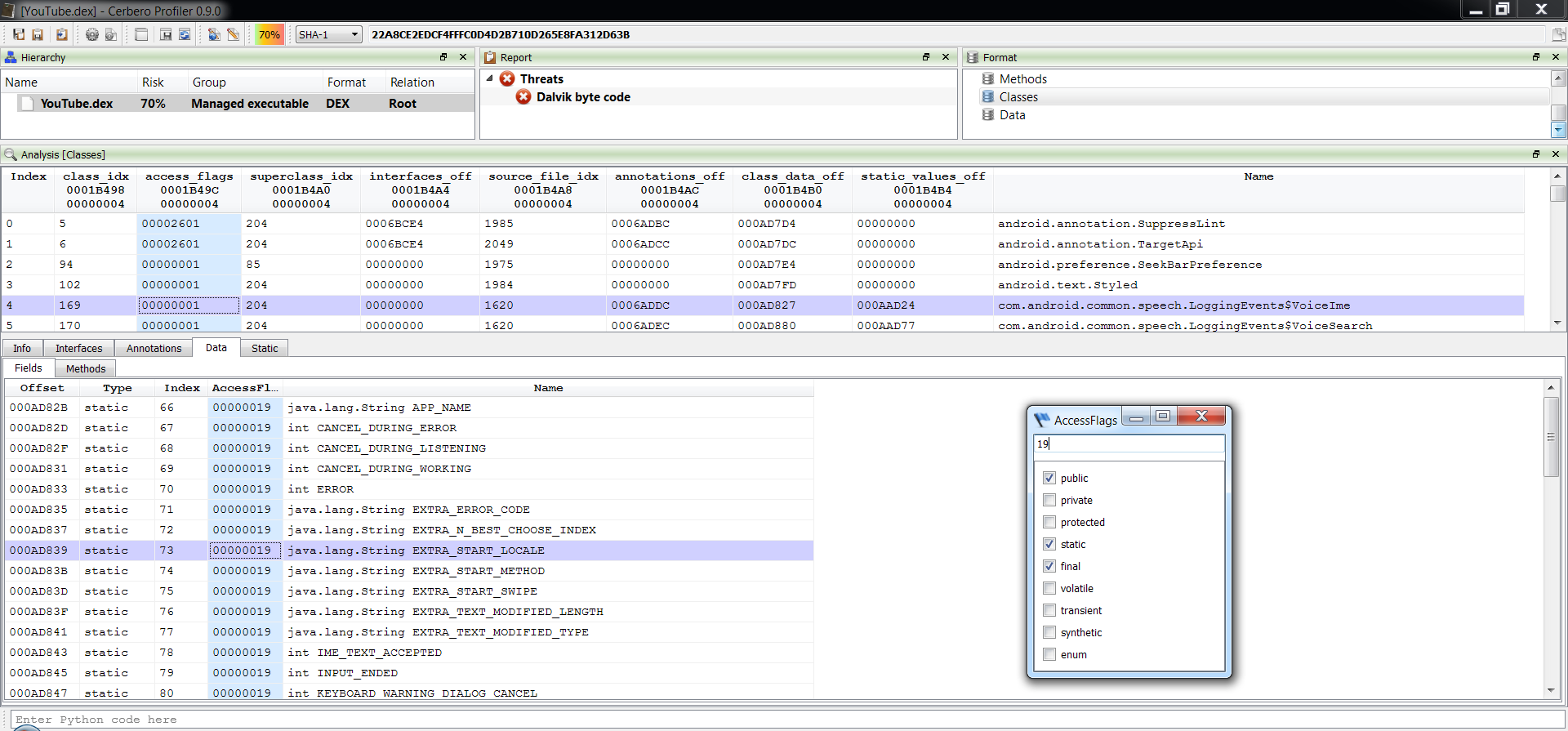
Also accurate layout ranges can help to analyze the format.
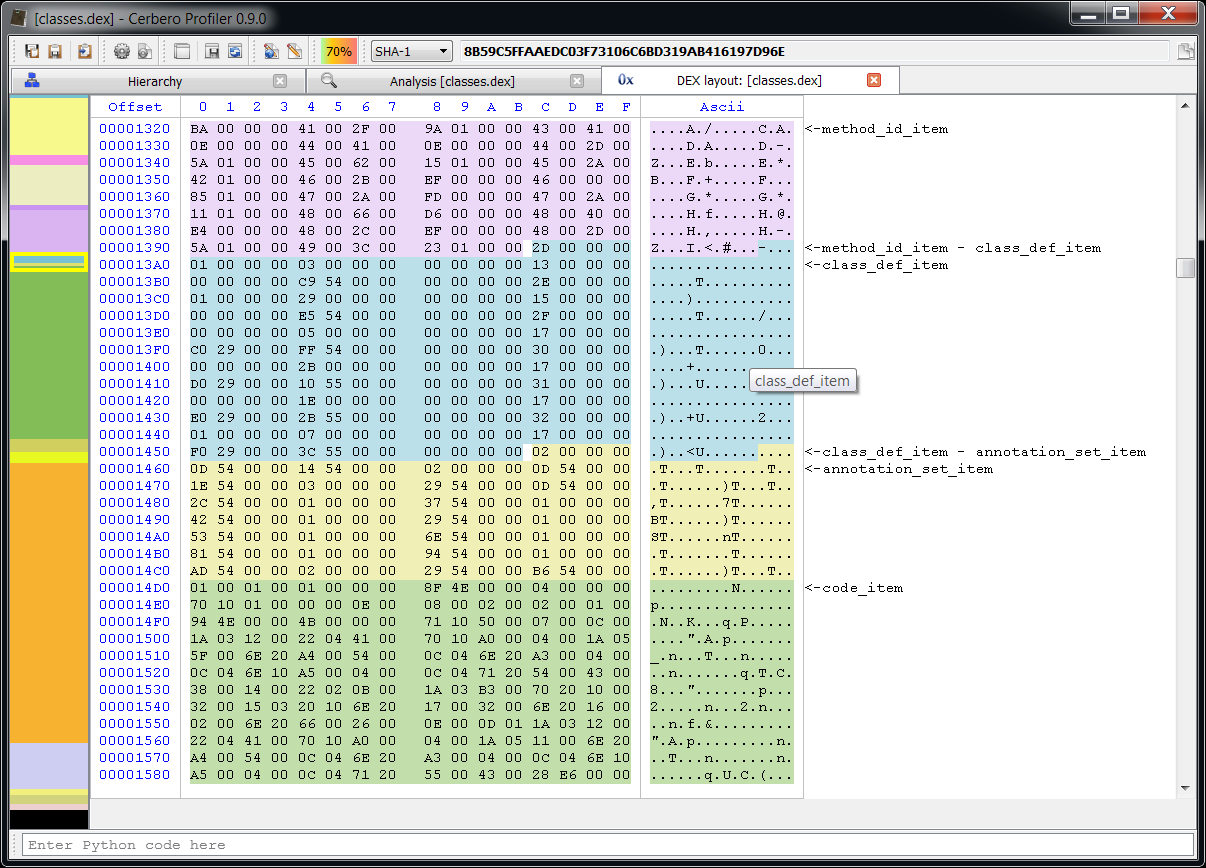
And finally a disassembler to quickly inspect the Dalvik bytecode.
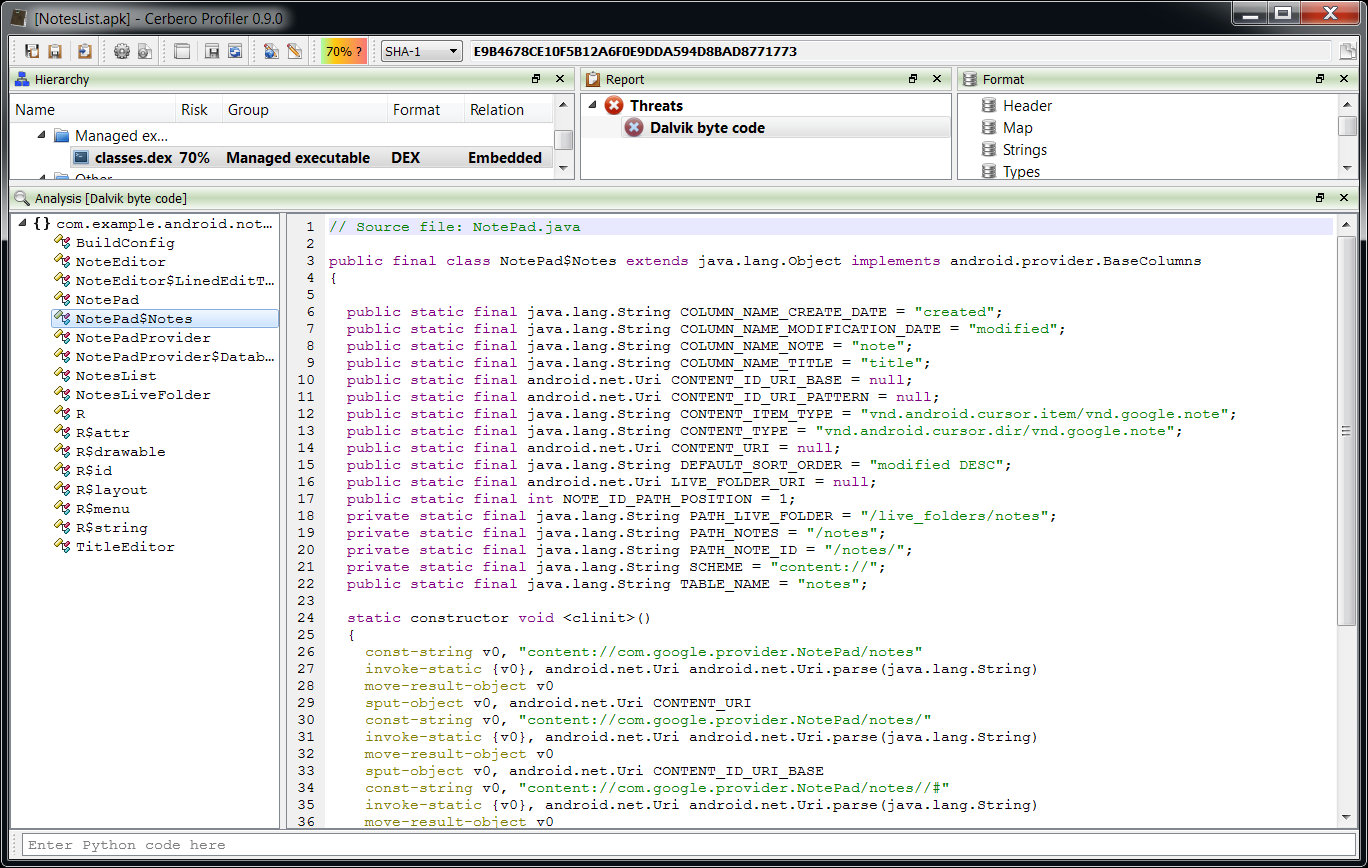
Here’s a disassembled function from the Android SDK NotePad sample:
private final void cancelNote()
{
const/4 v3, #int 0 // #0
iget-object v1, v4, android.database.Cursor mCursor
if-eqz v1, loc_74 // +34
iget v1, v4, int mState
if-nez v1, loc_90 // +38
iget-object v1, v4, android.database.Cursor mCursor
invoke-interface {v1}, void android.database.Cursor.close()
iput-object v3, v4, android.database.Cursor mCursor
new-instance v0, android.content.ContentValues
invoke-direct {v0}, void android.content.ContentValues.()
const-string v1, "note"
iget-object v2, v4, java.lang.String mOriginalContent
invoke-virtual {v0, v1, v2}, void android.content.ContentValues.put(java.lang.String, java.lang.String)
invoke-virtual {v4}, android.content.ContentResolver getContentResolver()
move-result-object v1
iget-object v2, v4, android.net.Uri mUri
invoke-virtual {v1, v2, v0, v3, v3}, int android.content.ContentResolver.update(android.net.Uri, android.content.ContentValues, java.lang.String, java.lang.String[])
loc_74:
const/4 v1, #int 0 // #0
invoke-virtual {v4, v1}, void setResult(int)
invoke-virtual {v4}, void finish()
return-void
loc_90:
iget v1, v4, int mState
const/4 v2, #int 1 // #1
if-ne v1, v2, loc_74 // -11
invoke-direct {v4}, void deleteNote()
goto loc_74 // -16
} And the original source for comparison:
private final void cancelNote() {
if (mCursor != null) {
if (mState == STATE_EDIT) {
// Put the original note text back into the database
mCursor.close();
mCursor = null;
ContentValues values = new ContentValues();
values.put(NotePad.Notes.COLUMN_NAME_NOTE, mOriginalContent);
getContentResolver().update(mUri, values, null, null);
} else if (mState == STATE_INSERT) {
// We inserted an empty note, make sure to delete it
deleteNote();
}
}
setResult(RESULT_CANCELED);
finish();
} Next week will be dedicated to fixing reported bugs and adding some small improvements. After that and some testing the new version should be ready, so keep tuned as the new version should be deployed soon!